have i been pwned Password Database
Date: Tuesday, July 24, 2022
Author: ICS Admin
Are you curious about the password database that you can download from have i been pwned?.
It contains a collection of known passwords from various data breaches. If you are security conscious and are working on an unsecured internet connection, you can download the database and check it offline instead of using the main search feature.
There is no other identifying information in the file.
The database export is greater than 10 Gigabytes.
To use this flat file, you can download it at: https://haveibeenpwned.com/Passwords (scroll down to the bottom of the page)
The file format begins with the known password converted to SHA1 (upper case) and how many instances it has been found.
Example
The password 12345678 has a SHA1 sum converted to uppercase of 7C222FB2927D828AF22F592134E8932480637C0D and was found 5119355.
Note: The data file had all values converted to upper case when dumped from the database.
The following instructions assume that you have downloaded the SHA1 file.
Once you have unarchived the database, you can test the various passwords in your list.
Password: ucanttouchthis
1) Open a Linux terminal (you can use a terminal in the Ubuntu Subsystem on Windows)
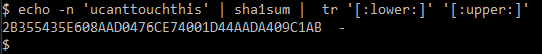
2) Using the echo command, convert the password to a SHA1 hash. Then, convert it to upper case.
3) Next, use grep to search for the SHA1 message digest (do not include whitespace or the hyphen) in the pwned password flat file.
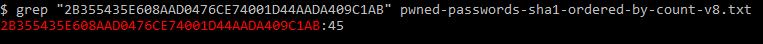
In this example, the password ucanttouchthis was found 45 times.
That's it.
It contains a collection of known passwords from various data breaches. If you are security conscious and are working on an unsecured internet connection, you can download the database and check it offline instead of using the main search feature.
There is no other identifying information in the file.
The database export is greater than 10 Gigabytes.
To use this flat file, you can download it at: https://haveibeenpwned.com/Passwords (scroll down to the bottom of the page)
The file format begins with the known password converted to SHA1 (upper case) and how many instances it has been found.
7C222FB2927D828AF22F592134E8932480637C0D:5119355
Example
The password 12345678 has a SHA1 sum converted to uppercase of 7C222FB2927D828AF22F592134E8932480637C0D and was found 5119355.
Note: The data file had all values converted to upper case when dumped from the database.
https://www.troyhunt.com/ive-just-launched-pwned-passwords-version-2/
The following instructions assume that you have downloaded the SHA1 file.
Once you have unarchived the database, you can test the various passwords in your list.
Password: ucanttouchthis
1) Open a Linux terminal (you can use a terminal in the Ubuntu Subsystem on Windows)
2) Using the echo command, convert the password to a SHA1 hash. Then, convert it to upper case.
echo -n 'ucanttouchthis' | sha1sum | tr '[:lower:]' '[:upper:]'

3) Next, use grep to search for the SHA1 message digest (do not include whitespace or the hyphen) in the pwned password flat file.
grep "2B355435E608AAD0476CE74001D44AADA409C1AB" pwned-passwords-sha1-ordered-by-count-v8.txt

In this example, the password ucanttouchthis was found 45 times.
That's it.
